Identities
Active Directory
Configure your Active Directory integration here.
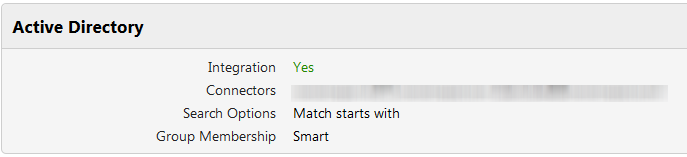
| Setting | Description |
|---|---|
| Integration | Enable this to allows client agents to connect with the user's Active Directory credentials |
| Connectors | By default, Smartcrypt uses the current Internet Information Server (IIS)/Machine account to connect to Active Directory. In this setting, you can (a) identify a different server account and (b) add one or more connected forests to permit searching across multiple forests. See Adding a Connection for details. |
| Search Options | Match contains (default) allows you to use wildcards at either end of the search term. ?xa* will find EXAMPLE, but not EXCEL Match starts with only accepts wildcards at the end of the search term. You cannot indicate one or more characters at the start with a wildcard. Searching for ex* will find EXAMPLE and EXCEL, but not AXIS. We recommend staying with the default search option for its flexibility and ease of use, but if domain searches take too long in your environment, Starts With has better performance. |
| Group Membership | Choose from Smart (default) or Exhaustive. We recommend staying with the default Smart option, as the Exhaustive option completely searches through all connectors for any user group membership query and consumes a high amount of resources. |
Adding a Connection
If you have AD users stored across multiple connected forests, you must add those forests to Smartcrypt Enterprise Manager here.
- Click Connectors to open the Active Directory Connections page. You'll see the current list of registered domains.
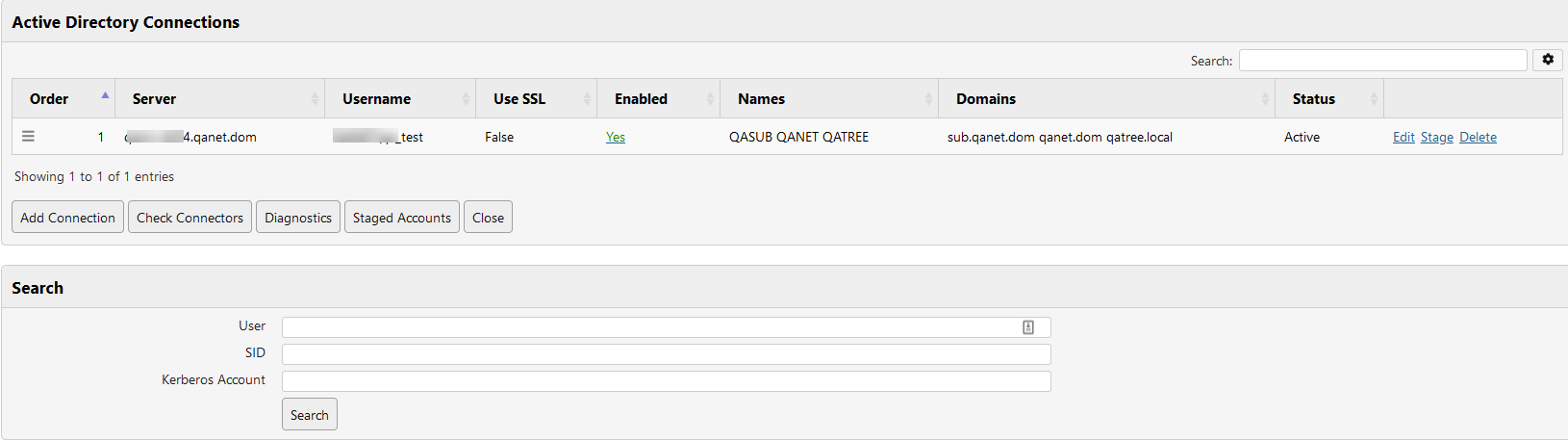
- Click Add Connection. The Add Forest Connector page displays.
- Enter the full name of the server you want to connect.
- Enter the username and password to connect to the server.
- Check Use SSL to connect securely. By default, the Enabled box is checked.
- The Enabled box enables or disables the connector for use by the manager, checked by default.
- Test the connection by searching for a UserID, Kerberos account, or SID on the new forest. Click Test to run the search.
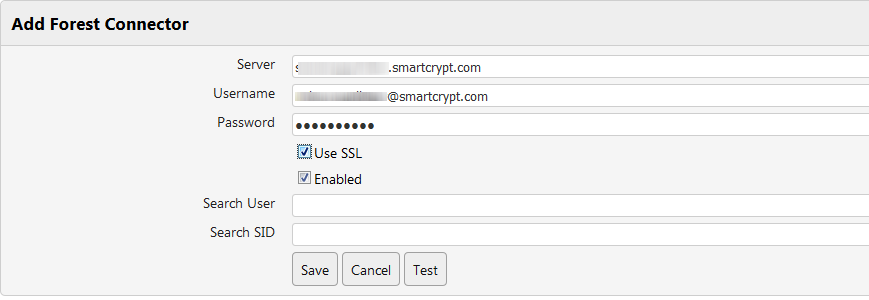
- When the server passes the connection test, click Save to add this domain account.
Note: If Smartcrypt Enterprise Manager fails to connect to an Active Directory Connector, SEM will disconnect and attempt to reconnect (retry) to the Connector. This establishes a clean connection. The failure will be logged. By default, only one connection retry is allowed. Contact your Smartcrypt system administrator if the problem persists.
Searching Forests
Use the Active Directory Connections page to search for a User or SID on all connected forests.
Note that you can define what forest Smartcrypt searches first with the Order column on the Active Directory Connections page. Drag and drop the icon for each server to change the current order.
Staging Accounts
In a large-scale Smartcrypt deployment you may want to pre-load some user accounts before they connect. The Stage option on the Active Directory Connections page gives you the ability to decrease load during the initial rollout.
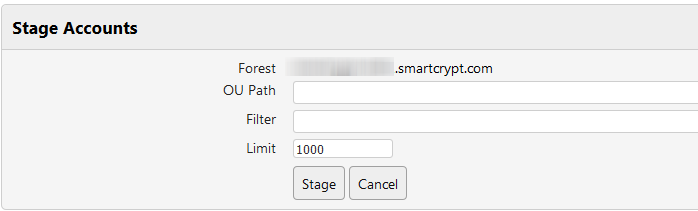
- Click Stage next to the Server you want to add accounts to.
- Define the path to the Organizational Unit you want to load accounts from.
- Use Lightweight Directory Access Protocol (LDAP) filters to specify what accounts to add. See Extracting Files in the Smartcrypt Command Line Interface user guide for more information on using LDAP filters.
- Specify a limit for the number of accounts to stage.
- Click Stage to start the process.
Click Staged Accounts on the Active Directory Connections page to review the existing Staged Accounts.
.png)