Dashboards
The PEM Administrator dashboards allow admins to quickly visualize, review and act on important data security intelligence (DSI) events. Admins can choose from a set of panels to customize dashboards to present the information in a way that is meaningful to them. To utilize Dashboards, it is recommended to enable Daily Reports from the Advanced > Reports page, and customers must configure one of two options detailed below. Dashboards can only be used with Elastic Search backends.
Using same target as DSI:
- From the Reporting > Config page, ensure that the 'Target Type’ in the “Edit Data Security Intelligence Policy" section is set to ‘elastic search’.
- From the Dashboard > Config page, ensure that the ‘Target’ is set to ‘same as DSI target’.
Using data from external Elastic Search:
- From the Dashboard > Config page, ensure that the "Same as DSI Target" is unchecked and fill in the URL and Index of external Elastic Search.
By default, two Dashboard are created automatically for the customers.
- System Dashboard: This dashboard contains information related to agents, users, key and archive policies that are currently deployed.
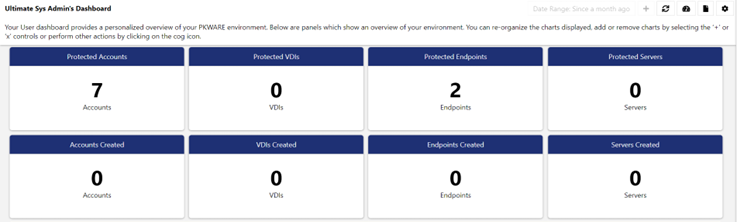
- Ultimate Sys Admin's Dashboard: This dashboard contains information related to accounts, VDIs, endpoints and servers created vs protected.
Dashboard Controls
The controls specified in this screen allows a user to add, edit, refresh, lock or unlock dashboard, etc. The data on the dashboard can be filtered based on the date range. Following are the controls:
Options | Description |
All | This shows all data, that has been compiled since the system was configured to produce dashboard reports. |
Absolute | This allows admins to configure an absolute time/ date range that will apply to the data in the charts. E.g., if you want to filter data for month of August 2022, then specify starting range from 1/08/2022 to 31/08/2022. |
Relative | This allows admins to configure a relative time / date range, that will apply to the data in the charts. E.g., if you want to filter data for the last 3 months, you can configure this date value from the drop-down fields. |
Add Panels
Click to add a panel. This will display the list of all the available panels. Select the panel you want to add and define the Properties in the dialog settings. Once the properties have been specified, click Add to Dashboard. Newly added and existing panels in a dashboard can be dragged and dropped to change their location in the dashboard. PKWARE has numerous pre-defined charts containing different data sets, which are organized under the following headings, based on the information they provide. They are:
- Archive
- Redaction
- Discovery
- General
- Classification
- System
- Double Key Encryption (DKE)
- Utility
Refresh Panel Data
Click Refresh
Export Panels
You can download the dashboard reports in PDF, PNG or CSV formats. To do so, click
Lock and Unlock Dashboard
You can lock and unlock dashboards for restricting and editing the description. The Lock feature allows you to lock the dashboard to restrict the editing features whereas the Unlock feature allows you to unlock the dashboard to edit the description or to add charts and graphs. To lock the dashboard, click
Dashboard Templates
PKWARE provides a set of specialized dashboards for customer use. Please refer Repository section for more information. To access pre-defined dashboard templates, click icon on the top right corner of the screen. This will redirect you to the Repository page where JSON files are stored for pre-defined dashboard templates.
Settings
The options listed in Setting allow you to add, edit, hide, delete, etc., the dashboards.
Options | Description |
Hide Description | This option allows you to hide description displayed at the top of the screen for the selected panel. |
Show Description | This option allows you to unhide description displayed at the top of the screen for the selected panel. |
New Dashboard | This option allows you to create a custom dashboard. |
Edit Dashboard | This option allows you to edit the description displayed at top of the screen. |
Delete Dashboard | This option will delete the dashboard by removing all panels and description. |
| Import JSON | This option allows you to import the file for the dashboard in the JSON format. |
| Export JSON | This option allows you to export the file for the dashboard in the JSON format. |
Add Filters to Existing Charts
You can add filters to existing charts by selecting criteria in the Filters section of the properties dialog. Once filters are defined, click Save to Dashboard to apply the filters, and the data in the existing chart is modified based on the criteria entered. You can access the properties dialog by selecting the 
Option | Description |
AD User (Active Directory) | Select an AD User from the drop-down and input the email address in the provided field. For example, administrator@pkware.com |
User Email | Select User Email from the drop-down and input the specific user's email ID in the provided field. For example, john.lenin@pkware.com |
File | Select File from the drop-down and input the name of a file in the provided field. |
Location | Select Location from the drop-down and input the folder path in the provided field. |
Action | Select Action from the drop-down and input the specific Remediation Action you would like to search for in the provided field. The available options are: Report - Files that triggered an action of Report based on the discovery of sensitive information. Decrypt - Files on which decrypt action was taken. MIP - Files on which Microsoft Information Protection (MIP) labels have been applied. Encrypt - Files on which an encrypt action was taken. Classify - Files on which PKWARE classification labels have been applied. Redact - Files on which redact action was taken. Delete - Files on which delete action was taken. Note: To learn more about each Remediation Action, visit Remediation. |
| Label | Select Label from the dropdown and input the name of the label created in the Device Profile screen. |
Pattern | Select Pattern from the drop-down and input the specific pattern name in the provided field. For example, Email Address, Credit Card Numbers, Social Security Number, etc. |
Definitions
Chart Name | Chart Information |
|---|---|
Encryptions | The number of encryption actions executed. Showing the total for each day, for the time range of the report |
Encryptions by Location | Encrypted files that contain the most sensitive items in them, with a slice showing the total number of sensitive items in each file (Top 10 files with most sensitive items) |
Encryptions by User | The number of encryption actions executed, with a slice showing the total for each unique user (Top 10 users based on number of encryption events) |
| Encryptions by Label | The slice of a pie chart shows the total number of encrypted files based on the table(s). |
Decryptions | The number of decryption actions executed. Showing the total for each day, for the time range of the report |
Decryptions by Location | Decrypted files that contain the most sensitive items in them, with a slice showing the total number of sensitive items in each file (Top 10 files with most sensitive items) |
Decryptions by User | The number of decryption actions executed, with a slice showing the total for each unique user (Top 10 users based on number of decryption events) |
Redacted Files | The number of files that were redacted. Showing the total for each day, for the time range of the report |
| Redaction by Labels | The slice of a pie chart displays the total number of redacted files based on the label(s). |
Redacted Emails | The number of emails that were redacted. Showing the total for each day, for the time range of the report |
Redacted Files by Pattern | The number of redacted files, with a slice showing the number for each discovery pattern that triggered the redaction (Top 10 patterns) |
Redacted Files by Location | Redacted files that contain the most sensitive items in them, with a slice showing the total number of sensitive items in each file (Top 10 files with most sensitive items) |
Redacted Files by User | The number of redacted files, with a slice showing the total for each unique user (Top 10 users based on number of redaction events) |
Redacted Items by Content Type | The number of items that were redacted, with a slice showing each type of content. For example: ‘Email Message Body’, ‘Email Subject’, ‘Email Attachment’ or a ‘File’ (Top 10 types) |
Emails with Redacted Subjects by Pattern | The number of emails whose subject was found to contain sensitive information and was redacted. With a slice showing each discovery pattern triggered. (Top 10 patterns based on the number of emails redacted) |
Emails with Redacted Message Bodies by Pattern | The number of emails whose message body was found to contain sensitive information and was redacted. With a slice showing each discovery pattern triggered. (Top 10 patterns based on the number of emails redacted) |
Emails with Redacted Attachments by Pattern | The number of emails whose attachment(s) was found to contain sensitive information and was redacted. With a slice showing each discovery pattern triggered. (Top 10 patterns based on the number of emails redacted) |
Emails with Redacted Subjects by User | The number of emails whose subject was found to contain sensitive information and was redacted. With a slice showing the total for each unique user. (Top 10 users based on number of emails) |
Emails with Redacted Message Bodies by User | The number of emails whose message body was found to contain sensitive information and was redacted. With a slice showing the total for each unique user. (Top 10 users based on number of emails) |
Emails with Redacted Attachments by User | The number of emails whose attachment(s) was found to contain sensitive information and was redacted. With a slice showing the total for each unique user. (Top 10 users based on number of emails) |
Discoveries | The number of discovery actions executed. Showing the total for each day; for the time range of the report |
Discoveries by User | The number of discovery actions executed, with a slice showing the total for each unique user. (Top 10 users based on number of discovery events) |
Discoveries by Location | Discover events on files that contain the most sensitive items in them, with a slice showing the total number of sensitive items in each file (Top 10 files with most sensitive items) |
Discoveries by Pattern | The number of discovery events executed, with a slice showing the number for each discovery pattern (Top 10 patterns based on number of discovery events) |
| Discoveries by Labels | The slice of a pie chart displays the total number of files discovered based on the label(s). |
Discovery Remediations by Action | The number of remediation actions taken, with a slice showing the number each unique remediation type. (Top 10 remediation types based on the number of actions taken) |
| Discovery Remediations by Label | The number of remediated actions taken, with the slice showing the number of each unique remediation type. |
Accounts Created | Number of accounts that were added to PK Protect within the time range of the report |
Protected Accounts | Total number of accounts that exist in PK Protect |
VDIs Created | Number of devices with a type of ‘Window Desktop Virtual’ (Virtual Desktop Instance), added to PK Protect within the time range of the report. |
Protected VDIs | Total number of devices with a type of ‘Window Desktop Virtual’ (Virtual Desktop Instance), that exist in PK Protect |
Servers Created | Number of Windows or Linux servers that were added to PK Protect within the time range of the report |
Protected Servers | Total number of Windows or Linux servers that exist in PK Protect |
Endpoints Created | Number of Windows, macOS, iOS and Android devices that were added to PK Protect within the time range of the report |
Protected Endpoints | Total number of Windows, macOS, iOS and Android devices that exist in PK Protect |
Manual Classifications | The number of files that were manually classified, showing the total for each day, for the time range of the report |
Manual Classifications by Label | The number of files that were manually classified, with a slice showing the total for each label. (Top 10 labels based on the number of classified files) |
Manual Classifications by Provider | The number of manual classifications based on the method used to classify the file. The method is the application from which the label was applied, like Word, Excel or file classifier (Top 10 methods based on the number of classified files) |
Manual Classifications by User | The number of files that were manually classified, with a slice showing the total for each user. (Top 10 users based on the number of files they classified) |
System Information | Shows information about the PEM Administrator, including: Application URL, Application Version, Number of Database Connections, Database Version, Used and available disk space, Operation System version, Uptime of the PEM Administrator application and the time at which Daily Jobs are run. |
Active Devices | The number of devices that synced with the PEM Administrator over the last 24 hours (current), the last week and the last month, based on the latest time in the time range of the report |
Agent Versions | The number of different agent versions deployed, with a slice showing the number for each agent version found, based on the latest time in the time range of the report (Top 10 agent versions based on the number of devices with each version) |
Active Users | The number of users that synced with the PEM Administrator over the last 24 hours (current), the last week and the last month, based on the latest time in the time range of the report |
Smartkeys | The number of Smartkeys defined in the PEM Administrator (excluding personal Smartkeys and Community keys), based on the latest time in the time range of the report |
Community Keys | The number of community keys defined in the PEM Administrator, based on the latest time in the time range of the report |
Archive Policies | The number of archive policies defined in the PEM Administrator Policy tab, based on the latest time in the time range of the report |
Agent Updates | The total number of times all the agents were updated, based on the latest time in the time range of the report |
Disk Space | The amount of free and used disk space for the server on which the PEM Administrator is running, based on the time at which the report was run |
Labeled Files | The number of files to which MIP labels were applied. Showing the total for each day; for the time range of the report |
Labeled Files by Name | The number of MIP labeling actions executed, with a slice showing the total number of files for each specific MIP label. (Top 10 labels based on number of labeling events) |
Labeled Files by User | The number of MIP labeled files, with a slice showing the total number applied for each unique user (Top 10 users based on number of MIP labeling events) |
Re-Labeled Files | The number of files for which MIP labels were changed. Showing the total number of re-labeling actions for each day; for the time range of the report |
Re-Labeled Files by Name | The number of files for which MIP labels were changed, with a slice showing the total number of files for each specific MIP re-labeling action. (Top 10 labels based on number of labeling events) |
Re-Labeled Files by User | The number of MIP labeled files that were re-labeled, with a slice showing the total number of re-labeling actions for each unique user (Top 10 users based on number of MIP re-labeling events) |
Labels Removed | The number of files MIP labeled files, where the labels were removed, such that they are now un-labeled. Showing the total for each day; for the time range of the report |
Label Removals by Name | The number of MIP label removal actions executed, with a slice showing the total number of files where labels were removed, indicating the prior label name. (Top 10 based on number of label removal events) |
Label Removals by User | The number of files where MIP labels were removed, with a slice showing the total number of MIP label removals for each unique user (Top 10 users based on number of MIP label removal events) |
.png)
