Windows: Encrypt with Lockers
PK Endpoint Agent Lockers run as a Windows Service. This provides an unattended automatic startup and protection after the application is installed and configured. If the file system can be mounted by a client that can run the PK Endpoint Agent, a locker can be used to automatically protect the data on the volume. Lockers can be run by admin and non-admin users.
On this page:
Locker Service Configuration On Windows Device Joined to the Domain
After installing the the PK Endpoint Agent client onto the system, open the PK Endpoint Agent Options, and click the Lockers tab
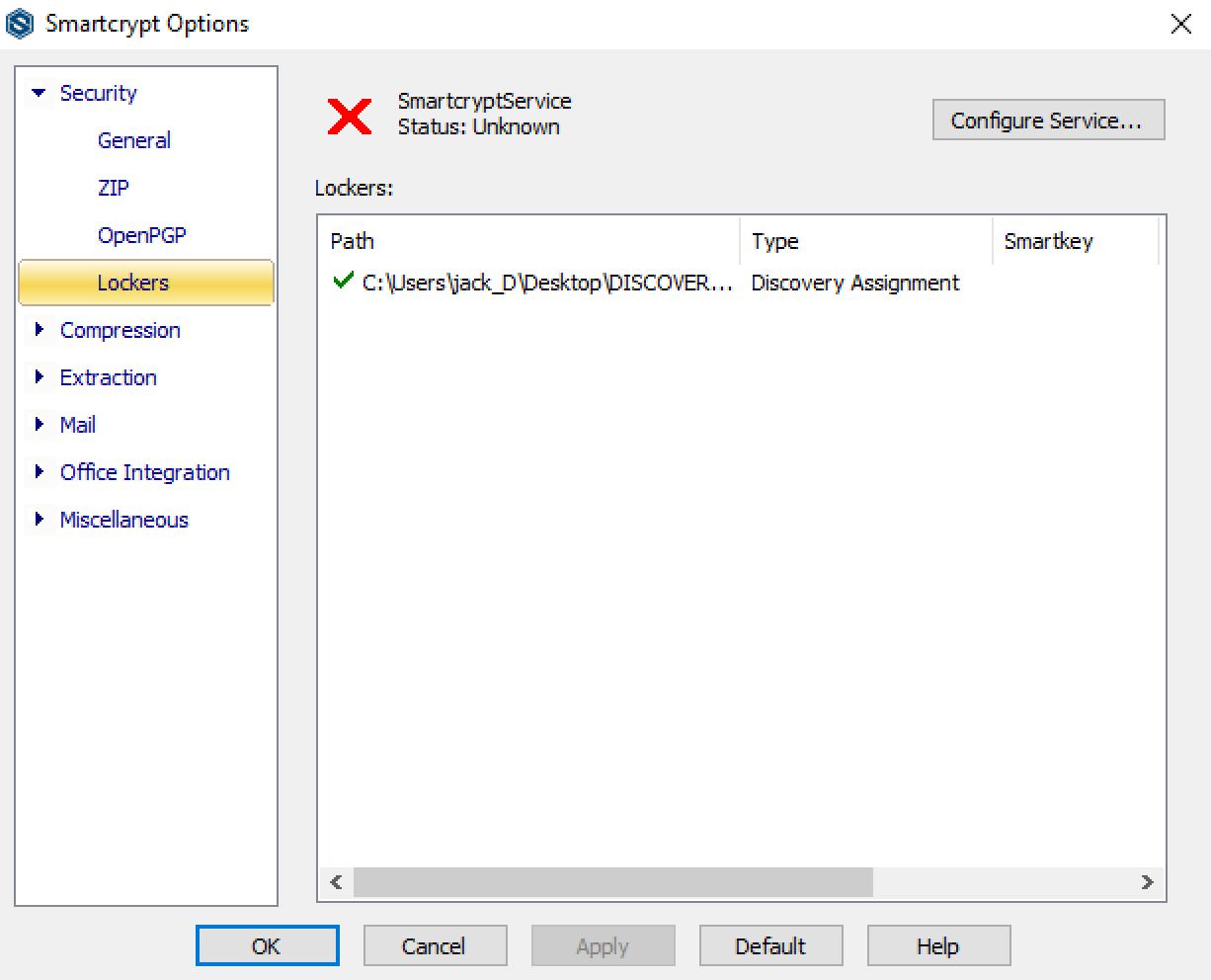
- Click Configure Service. A dialog will open that requires the current logged-in user to enter their password. After supplying the password, click OK.
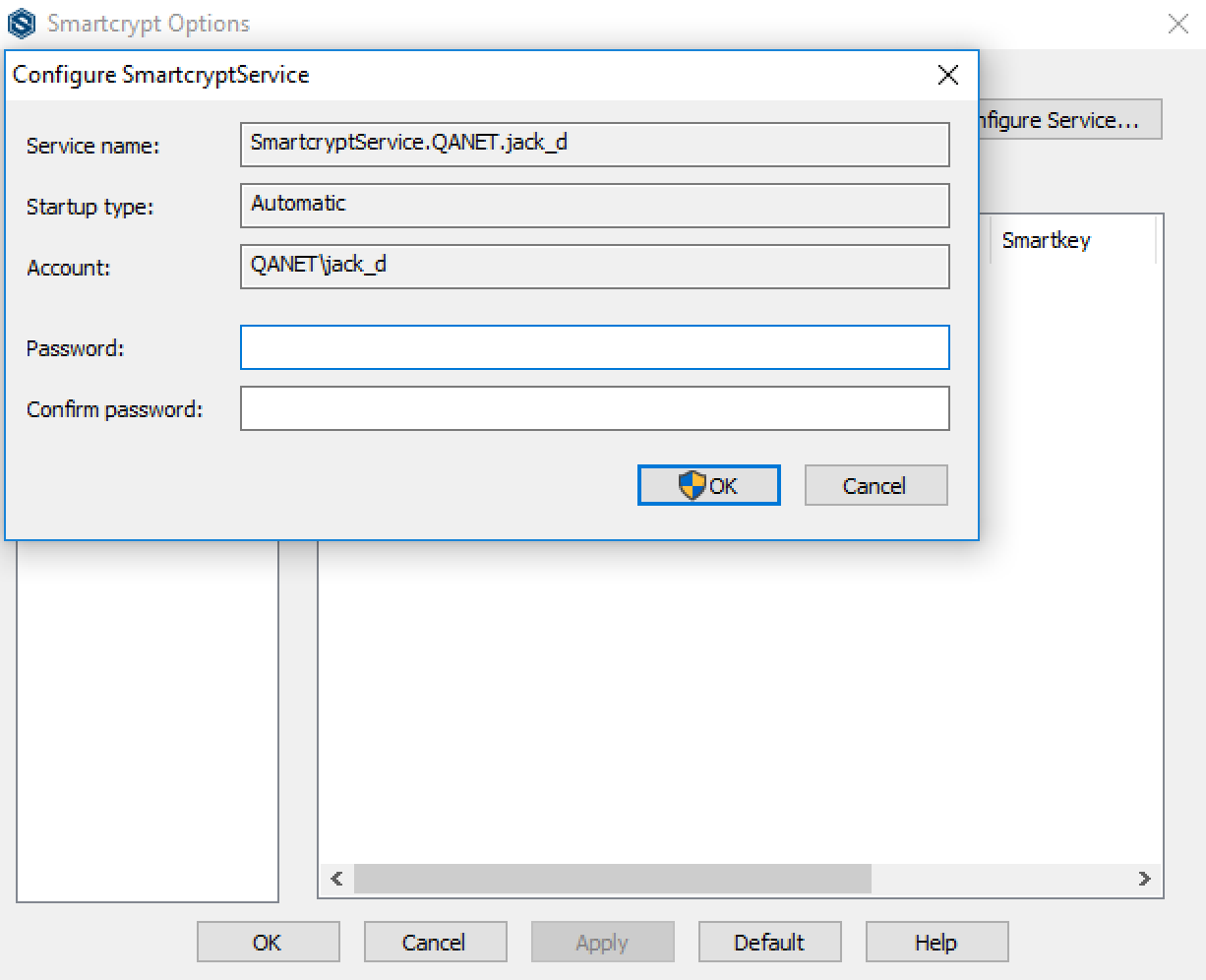
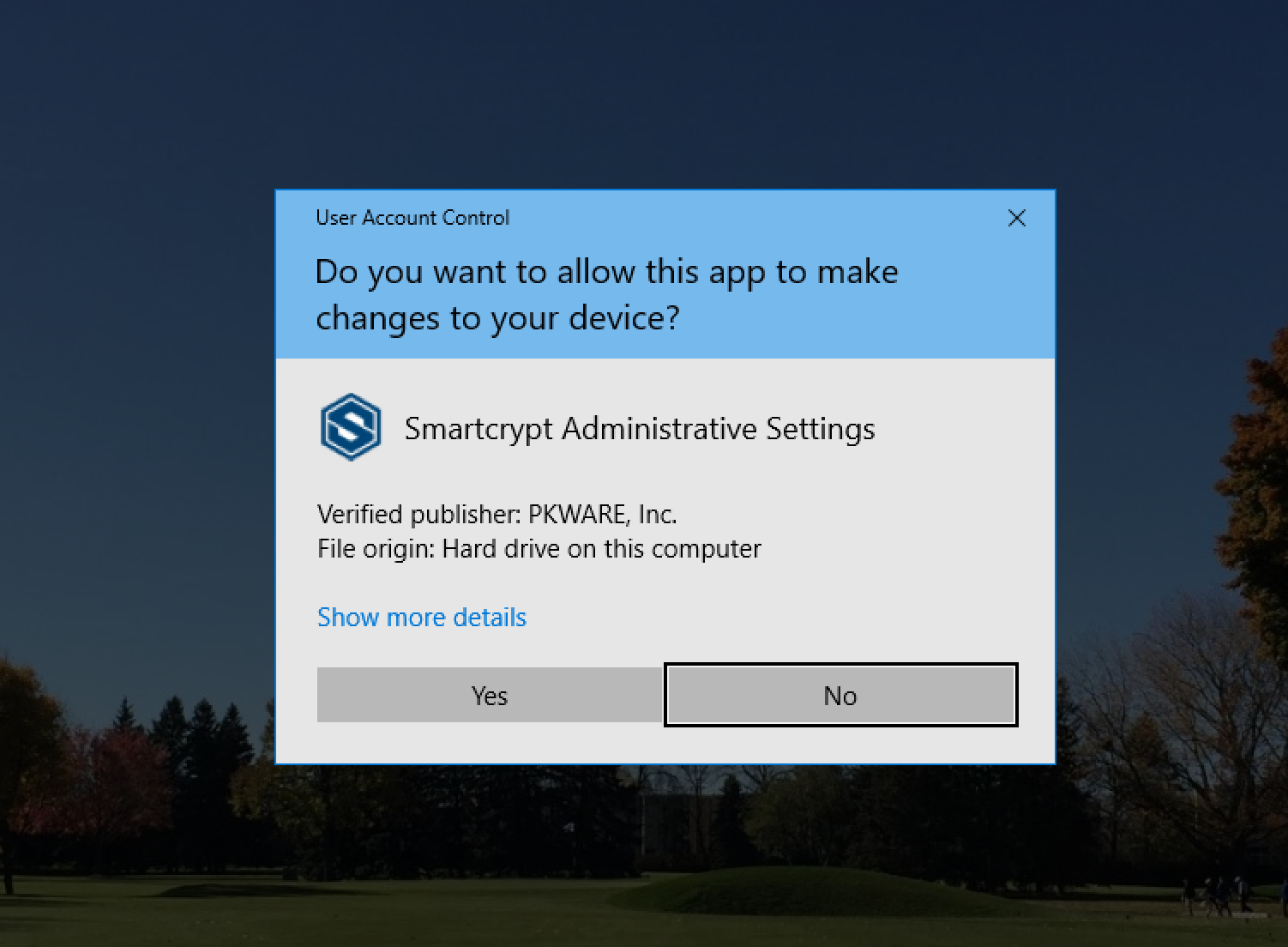
- Creating a Windows Service requires Administrator Privileges. Click Yes on this screen.
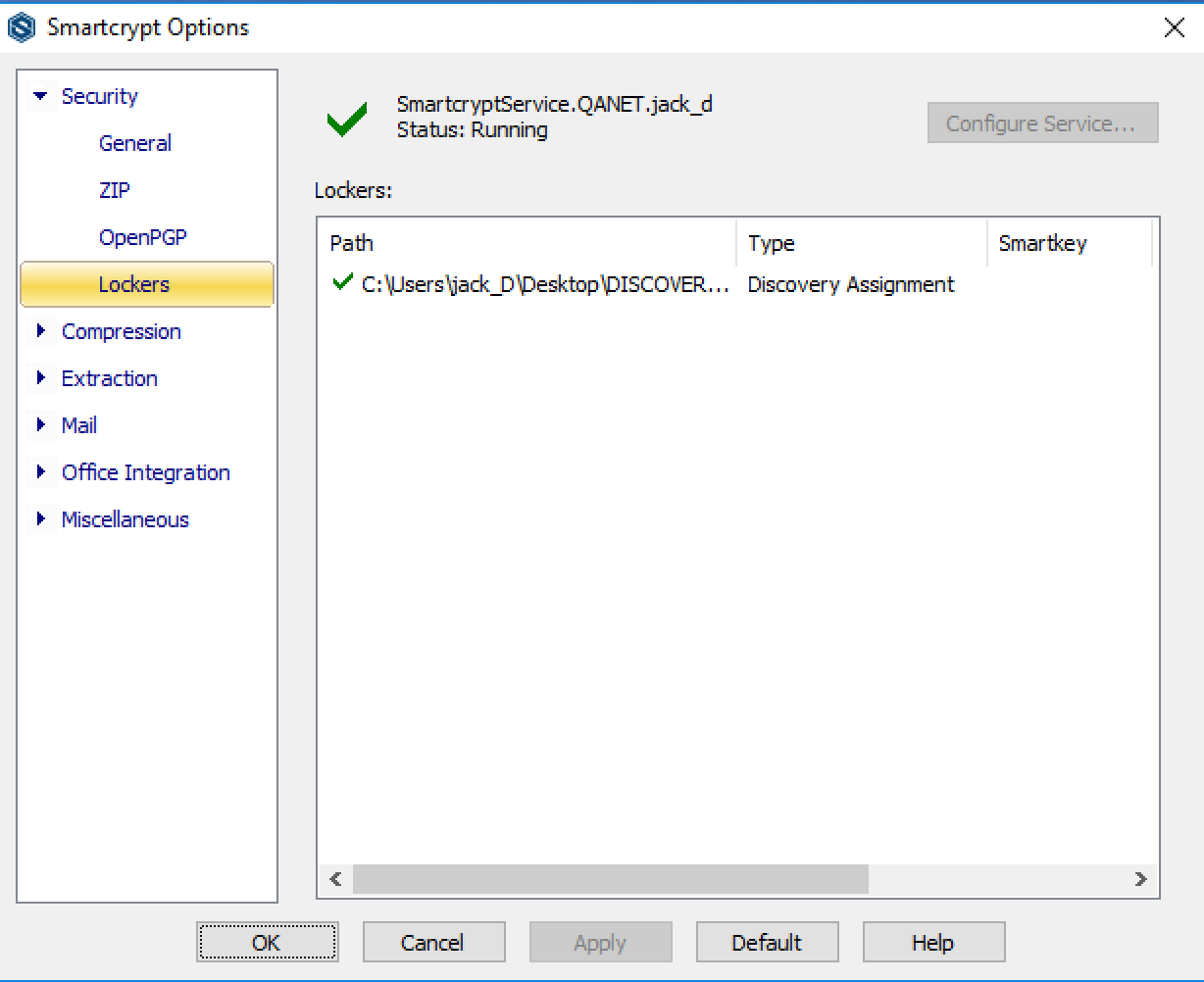
- In the PK Endpoint Agent Options, you will see the the PK Endpoint Agent Service was created and shows the current status:
Locker Service Configuration On Windows Device Not Joined to the Domain
A Windows device not joined to the domain can still be used with the PK Endpoint Agent Lockers. There are a few different setup constraints that this setup relies on, so it is important to follow these instructions when using Lockers on a machine that is not joined to the domain.
- Find the PK Endpoint Agent Agent icon in the task tray, and select Login:
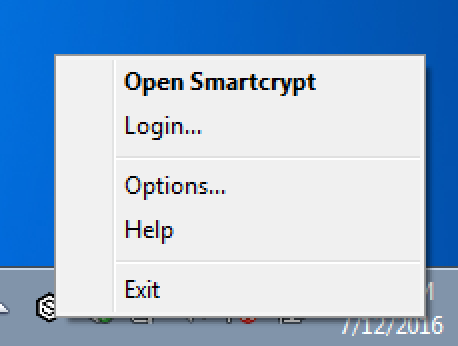
Since this machine is not using Active Directory credentials to log in with Windows, the PK Endpoint Agent needs a user to manually log in to store the PK Endpoint Agent credentials on the machine in the secured Credential Manager. - After seeing the log in prompt, enter your email address or if no email in your lab exists, enter the User Principal Name (UPN). A familiar Windows authentication window will open to have you authenticate with your Active Directory credentials again.
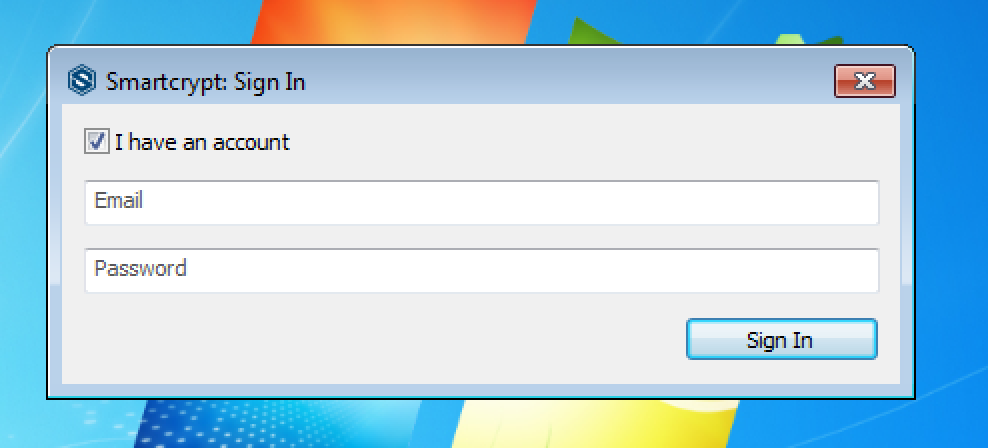
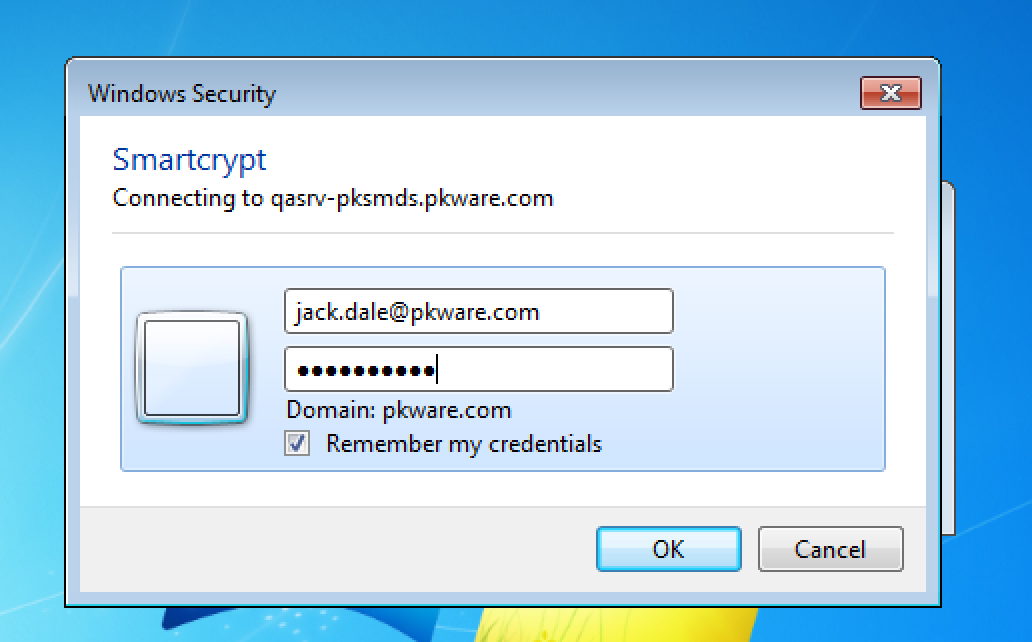
- (Optional) After successfully logging in, we can verify that the PK Endpoint Agent Credentials used to access the PK Endpoint Agent have been successfully stored to your local system account in Credential Manager. Open the Control Panel, then open Credential Manager to confirm the PK Endpoint Agent Credentials existence
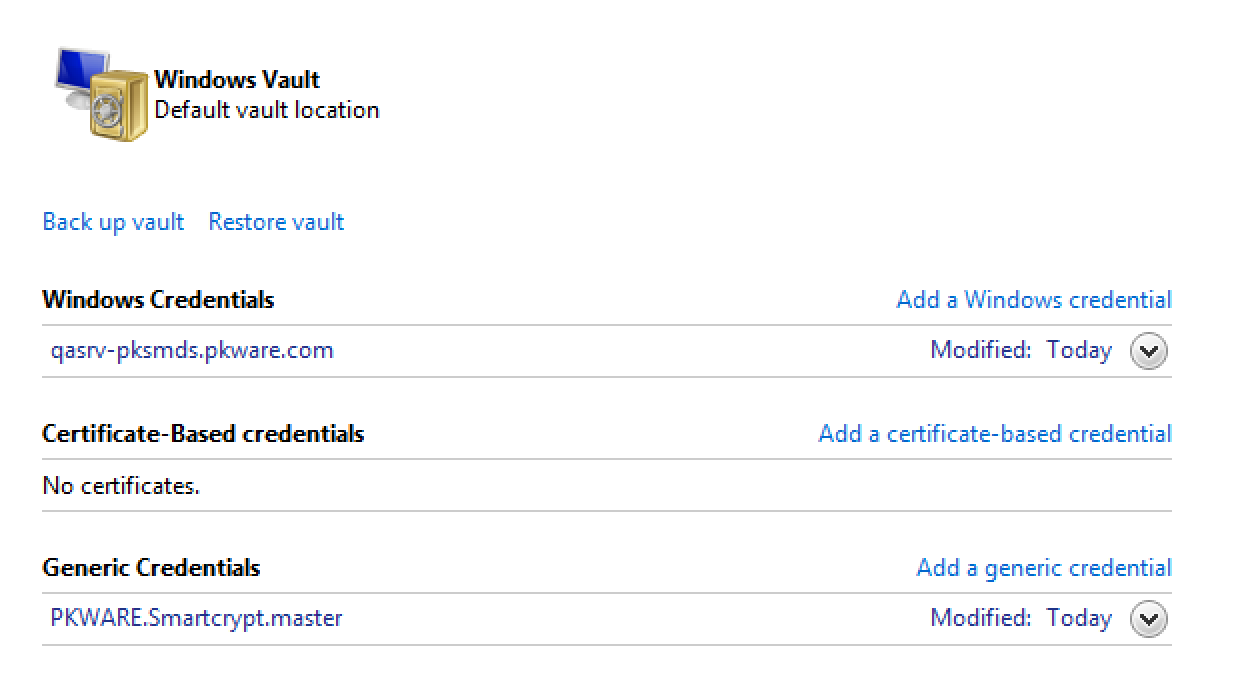
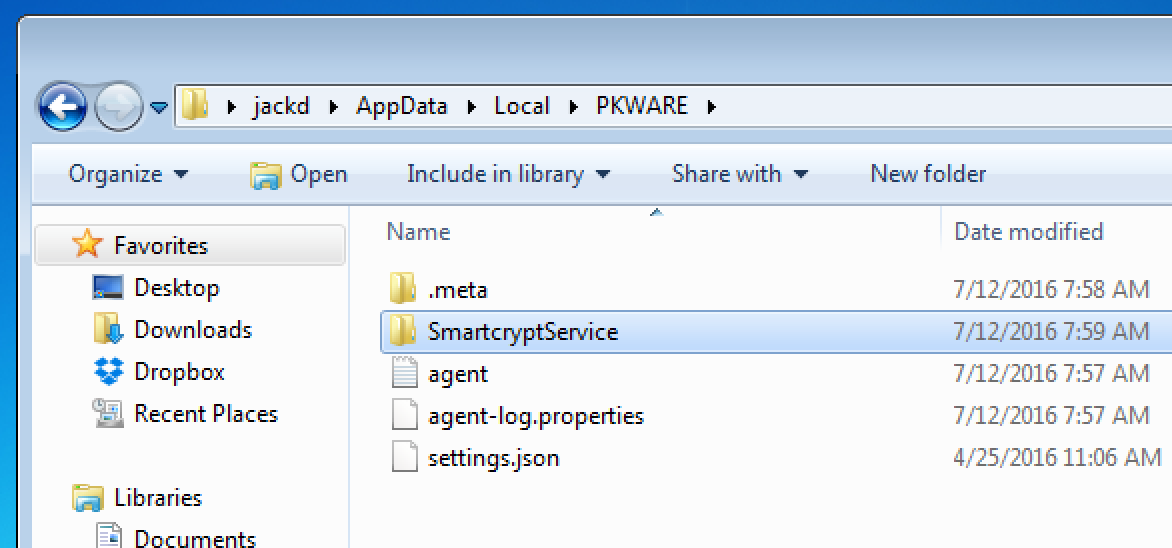
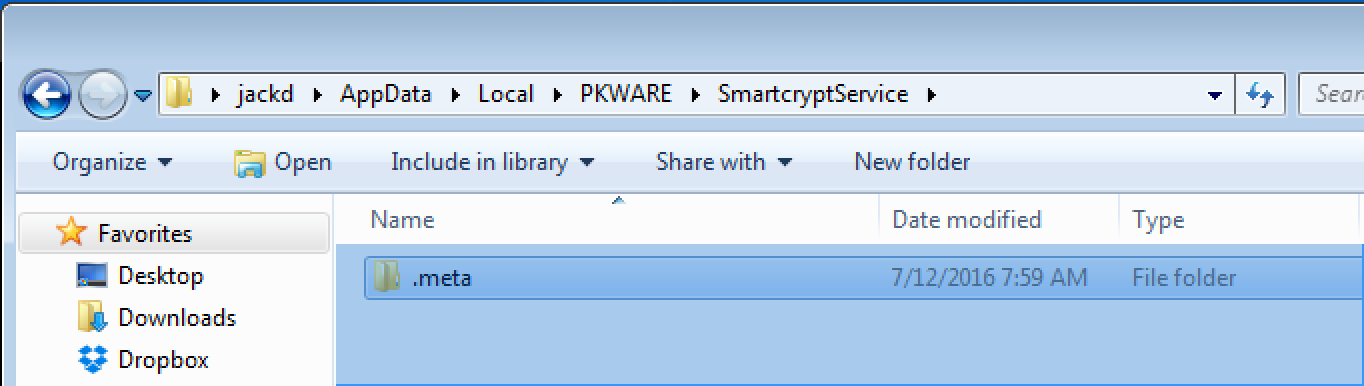
Now my local system account has credentials, I can manually copy the PK Endpoint Agent metadata folder into the PK Endpoint Agent Service directory. This still will enable the PK Endpoint Agent Service to login. To Log in, the service needs the Metadata, and the stored Credentials. Open the %localappdata%\PKWARE folder. - Make a new folder called SmartcryptService. Then copy the .meta folder into the SmartcryptService folder.
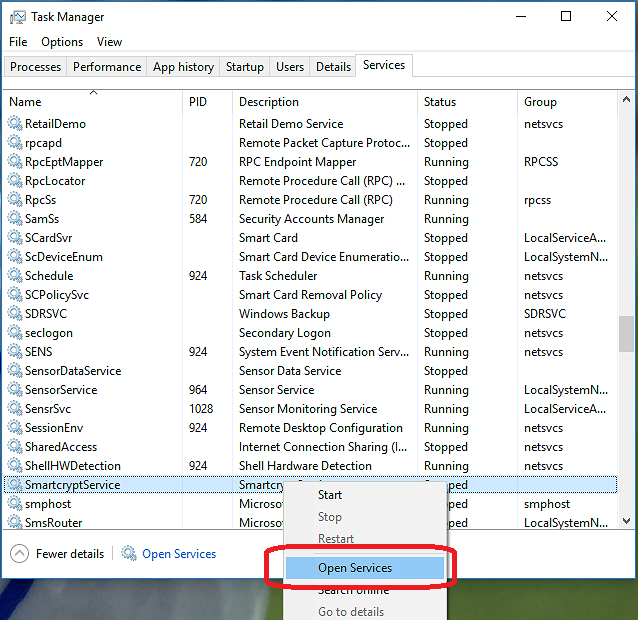
- Open the Task Manager on the machine and load the Services tab.Confirm that you see an entry called SmartcryptService. After finding it in the list of services, Right-click and select Open Services.
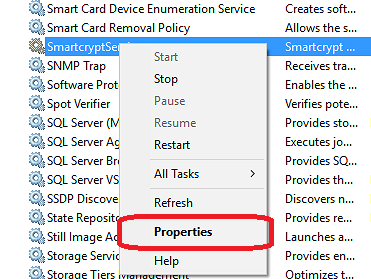
- In Windows Services Snap-in that opens, find SmartcryptService, right-click the service and select Properties.
- In the SmartcryptService, we need to set up login credentials for authentication with PK Endpoint Agent. There are also different startup options for Windows Services. In the General tab, define the Startup type value. Selecting Automatic will enable the Service automatically when the machine is powered on. Manual will require you the user to start / stop the service manually, so it is recommended to select Automatic.
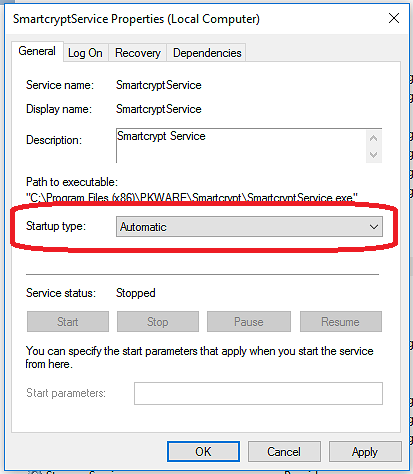
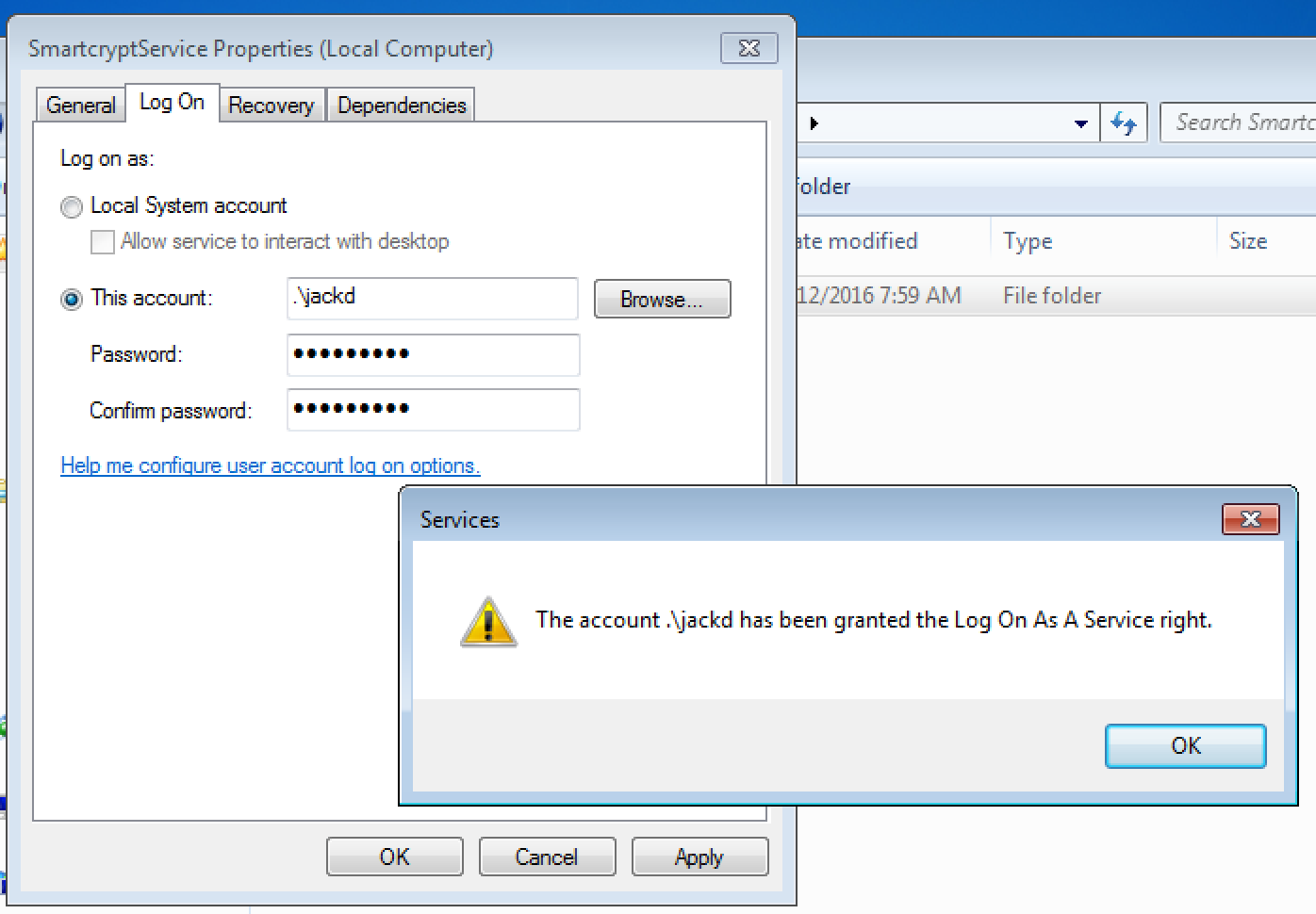
Next we need to make sure that the Windows Service authenticates with the PK Endpoint Agent as the appropriate local user. In the Log On tab, enter the credential used to log in with Windows on the device. Since you have stored the PK Endpoint Agent Credentials for this local system user account, and moved the metadata into the correct directory, the Smartcrypt Service will be able to authenticate the local account with a PK Endpoint Agent Account. If you haven't set up the Locker in PK Endpoint Manager yet, you might want to check out Creating a Smartcrypt Locker, as a Locker needs to be defined in the Manager before it works on the client.
Adding a Locker Service on Windows
If you desire to have more than one PK Endpoint Agent user to have a protected folder on a device, you need a separate Locker Service running on that device. To manually create the Windows Service:
In an elevated Command Prompt (cmd), run the following command to create a new Windows Service called "Locker Service For User A" :
sc create "Locker Service For User A" binpath= "C:\Program Files (x86)\PKWARE\Smartcrypt\SmartcryptService.exe """Locker Service For User A""""If you see this error, you are not elevated to Administrator Command Prompt.
[SC] OpenSCManager FAILED 5:
Access is denied.After creating a new service, you will need to configure it in the Windows Services Manager, just like 9660937
Deleting a Locker Service On Windows
In an elevated Command Prompt (cmd), run the following command to delete the existing Windows Service called "Locker Service For User A".
sc delete "Locker Service For User A"If you see this error, you are not elevated to Administrator Command Prompt.
[SC] OpenSCManager FAILED 5:
Access is denied.More information on Windows Services can be found here: https://technet.microsoft.com/en-us/library/cc755249(v=ws.11).aspx
More information on creating a PK Endpoint Agent Locker in the PK Endpoint Manager can be found here: Creating a Smartcrypt Locker
.png)