Guest Accounts
Smartcrypt Manager integrates with your Active Directory (AD) for identity and access management. All Smartcrypt user credentials come from AD. The security groups a user belongs to can also dictate what Smartcrypt policies or rules apply. When an administrator creates a user account, Smartcrypt will look for the user in a few different places.
AD User Email Address
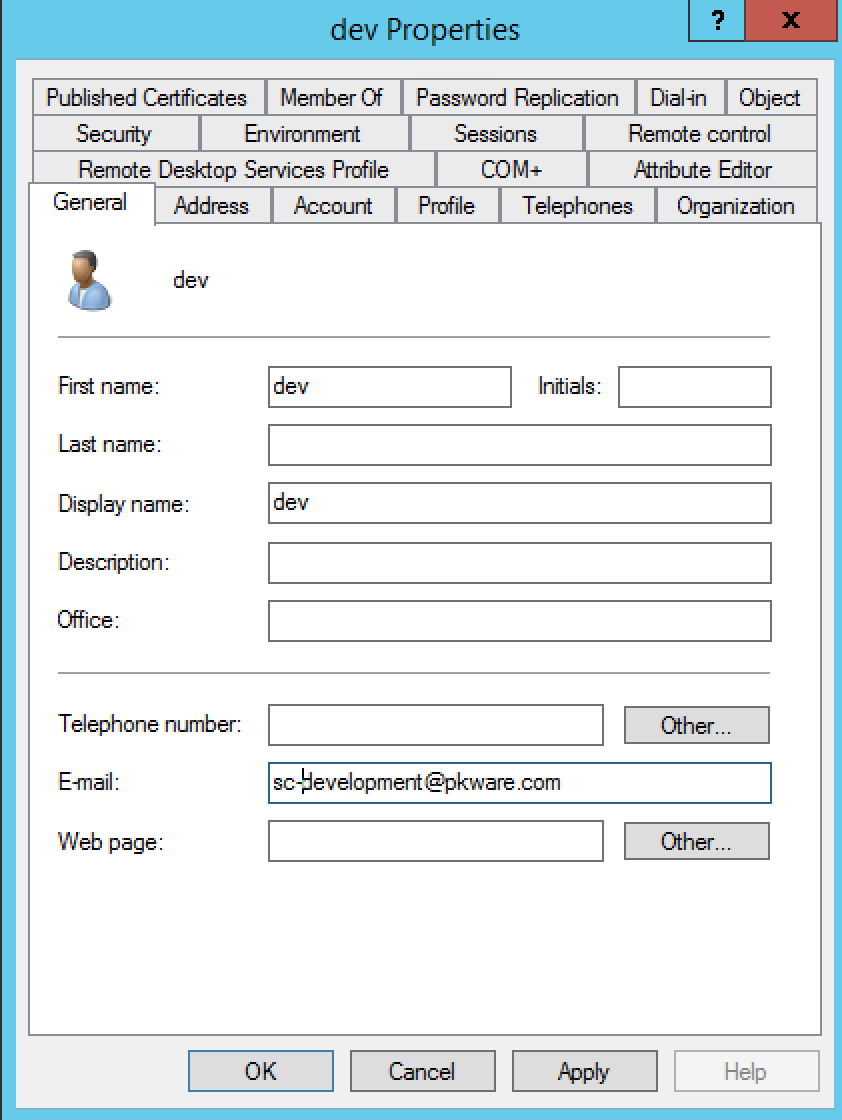
First, Smartcrypt will look for an email address defined for their AD User Object. Smartcrypt will then create an identity for that AD user, using the AD password to authenticate the account on the client. In the above screenshot, the account would be created with the sc-development@pkware.com address.
User Principal Name
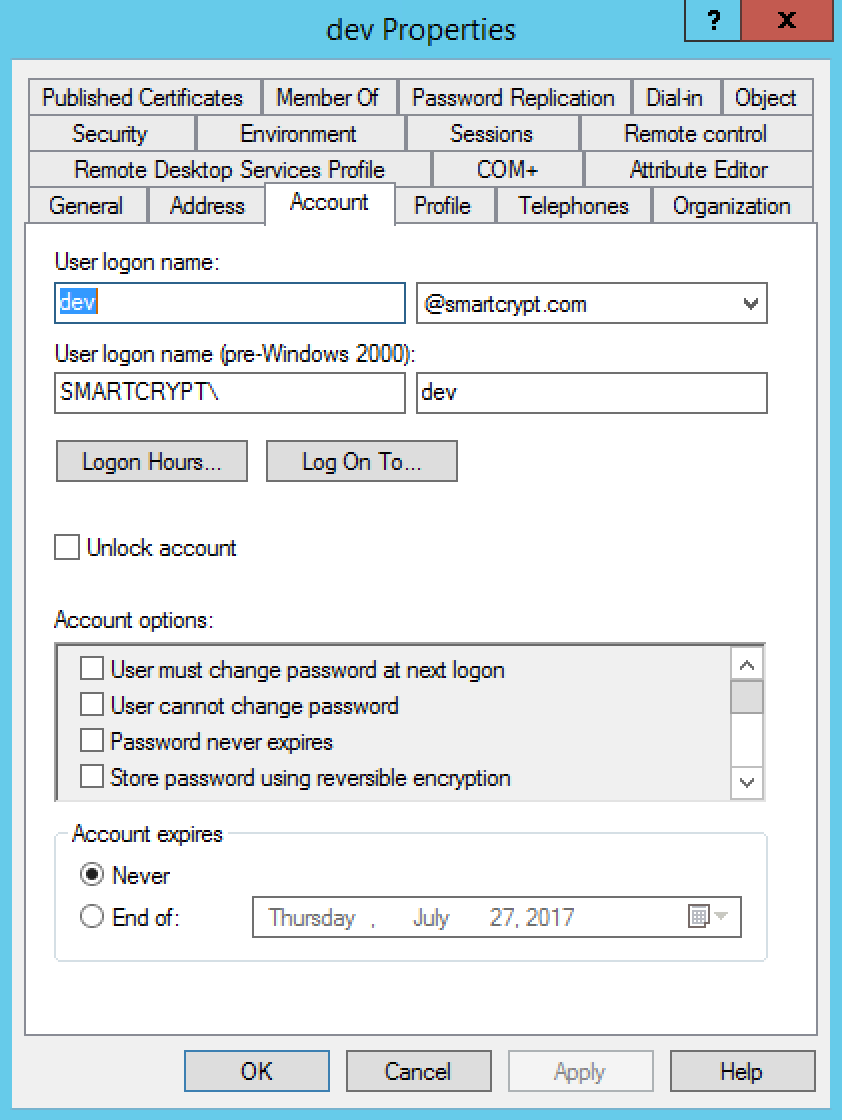
If an email address for the new Smartcrypt user is not in AD, Smartcrypt will fallback to using the User Principal Name (UPN) defined for the user account. This creates what looks like an email address by combining the user logon name and the domain suffix for the domain the user belongs to. In the above screenshot, the account would be created with the pseudo-address dev@smartcrypt.com, even though it is not an email address. It becomes the way to address the dev Smartcrypt User. Users connected to Smartcrypt Manager through UPN must belong to an Authorized Domain to have the same privileges as an AD user.
Authorized Domains
Across your Smartcrypt Ecosystem you might have any combination of user accounts with UPN or Emails being used.
When Smartcrypt Manager is set up and authenticated, the Smartcrypt Cloud delivers a list of Authorized Domains to Smartcrypt Manager. If a user's email address comes from an authorized domain, the account is confirmed for external sharing. This means that a user belonging to an authorized domain on a Smartcrypt Manager can create and use Smartkeys to share data with people outside the organization.
Guest Accounts
If a Smartcrypt administrator creates a user with an email address that can't be authenticated through the organization's Active Directory, and is NOT in a Smartcrypt authorized domain, a Guest account will be created. Guest users cannot share encryption keys with the outside world.
The following example illustrates the differences between user accounts.
Guest Account Example Scenario
Smartcrypt Manager Authorized Domains List:
smartcrypt.com, pkware.com
User 1:
Email: Unavailable/not in AD
UPN: crypto@pkware.com
User 2:
Email: crypto@gmail.com
UPN: crypto@gmail.com
User 3:
Email: keys@smartcrypt.com
UPN: keys@qa.local
Account Status
| Identifier | Identity Mapper | Status |
|---|---|---|
| User 1 | UPN | Authorized Account - The UPN has pkware.com which is an authorized domain for the Smartcrypt Manager |
| User 2 | Guest Account - The Email address is defined and does not match one of the authorized domains for the Smartcrypt Manager | |
| User 3 | Authorized Account - The Email address includes smartcrypt.com, which is an authorized domain for the Smartcrypt Manager, even though the UPN is not in the authorized list |
Authorized Account vs. Guest Account
There are some differences between the types of accounts. In general, there are configuration options that can be used to narrow the gap to provide a similar user experience for Guest accounts.
| Both Accounts | Authorized Account | Guest Account |
|---|---|---|
|
|
|
.png)