Basics
Use the Smartcrypt Enterprise Manager (SEM) Basics tab to complete the registration process and configure system integrations. Depending on the desired environment, different Smartcrypt components will need to be configured.
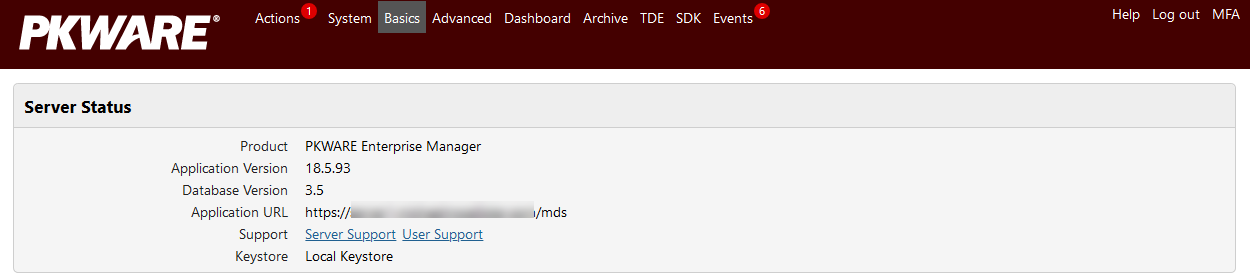
Viewing the Server Status
PKWARE Support uses the Server Status information to diagnose incidents and problems. Server Status provides a read-only view to the versions of your Smartcrypt Enterprise Manager application and database. The Support field allows you to download a Diagnostic Package with server or user logs in a .ZIP file. When contacting PKWARE for support, please include this package.
Click Server Support to download current logs for this Smartcrypt Enterprise Manager instance.
Click User Support and select a system user to download logs for that user.
Before registering the Smartcrypt Enterprise Manager, configure your Keystore. By default, Smartcrypt selects the local keystore configured during the install. Click the pencil to select from a Trusted Security Foundation if you are integrating Smartcrypt with QLabs, or a PKCS#11-based keystore. Paste your PKCS#11 keystore configuration file in the provided area.
Registering the Smartcrypt Manager
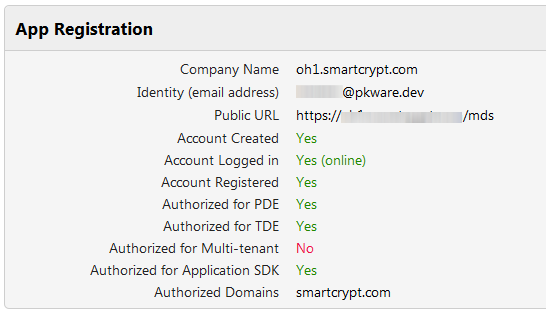
The Smartcrypt Enterprise Manager needs to be registered before it can function. The registration process alerts PKWARE that your SEM is online and ready for activation and licenses. A Public URL is required in this process to direct future traffic to this SEM. Once the SEM is registered with PKWARE, all users with a Smartcrypt-associated email domain will be directed to use the server for all Smartcrypt actions.
| Setting | Description |
|---|---|
| Company Name | Your company name. Click the pencil to edit this. |
| Identity (email address) | Your Smartcrypt Enterprise Manager connects to the Smartcrypt Cloud for licenses and updates through the Identity email. This account also facilitates key management to external users through the Smartcrypt Cloud. |
| Public URL | The external URL for the server. For those who are accessing your SEM outside of your network, this value is the publicly routable DNS entry. |
| Account Created | Is there a site account? When you have created a site account, this field displays Yes. If not, you must create one. See Creating an Online Account and Creating an Isolated Account for differences in the account types. |
| Account Logged In | Connected to Smartcrypt Cloud (online) or Isolated site account created (isolated). |
| Account Registered | Domain account is registered. |
| Authorized for PDE | This is the basic Smartcrypt service. Your account will zip and encrypt sensitive data based on policy. |
| Authorized for TDE | Server has Transparent Data Encryption (TDE) enabled. |
| Authorized for Multi-tenant | This feature permits compartmentalizing administration of a TDE server. |
| Authorized for TDE Desktop | |
| Authorized for Application SDK | The Smartcrypt Software Development Kit permits creating custom applications for Smartcrypt. |
| Authorized Domains | Domain name(s) allowed to access this Smartcrypt Manager. This will be completed after the initial account is created on the Smartcrypt Cloud. The list also controls which users are authorized users and Guest Accounts. |
Creating an Online Account
Creating an online account will allow your Smartcrypt Enterprise Manager to periodically sync with the Smartcrypt Cloud.
Create an online account if...
- You would like to allow internal users in your Smartcrypt environment to create and use Smartkeys with people outside the organization (external users).
- You would like external users to create and use Smartkeys with internal users.
- You would like to automate the site registration and license acquisition process.
Note: Regardless of whether you choose and Online or Isolated account, Internal users (people inside your organization) can always exchange Smartkey-encrypted files with each other. Depending on the policies you set, internal users can also exchange data encrypted with passphrases or public keys (X.509 or OpenPGP). You must create an online account to use Smartkeys with people outside your organization.
Registering an Online Server
To complete an online registration, just click the Create Account Online button after filling in the registration details. Your account will be created in the Smartcrypt Cloud and licenses will be synced down to your environment after the Smartcrypt Cloud defines them for your site.
Creating an Isolated Account
Creating an isolated account will configure the Smartcrypt Enterprise Manager to not sync with the Smartcrypt Cloud. Registration and licensing is completed in a manual out-of-band communication. You will need to export some JSON data and send it to PKWARE. Then PKWARE will send back JSON data to import.
Create an isolated account if...
- You will never allow Smartcrypt users to use Smartkeys with external users.
- You would like your SEM to not connect to the Smartcrypt Cloud.
Note: Regardless of whether you choose and Online or Isolated account, Internal users (people inside your organization) can always exchange Smartkey-encrypted files with each other. Depending on the policies you set, internal users can also exchange data encrypted with passphrases or public keys (X.509 or OpenPGP).
Registering an Isolated Server
- Under App Registration, enter a site registration fields.
- Click Create Account Isolated. This button creates the site account and logs it in to the database. The Logged In field will read Yes (Isolated mode).
- Click the Export Satellite Identity link that appears. You will be taken to a separate screen to download a server registration file.
- Copy and send that file back to PKWARE to register your Smartcrypt Enterprise Manager.
- PKWARE will generate an authorization file and send it back to you.
- Click Import Authorizations and specify the location of the authorization file from step 5.
Importing an Isolated Server License
As with the registration code, PKWARE will provide a license key to permit your company to use Smartcrypt (Server and Client). To install this code and make Smartcrypt operational:
- Copy the license text.
- Go to Advanced > Licenses .
- Click Import License.
- Paste the license text into this page.
- Click Import License.
The license will appear under Active Licenses.
General Configuration Options
You can configure many Smartcrypt Enterprise Manager processes here. Some settings control client activities, while others define how Smartcrypt Manager interacts with its ecosystem.

Setting | Description |
|---|---|
External Polling Interval (seconds) | How often (in seconds) Smartcrypt Enterprise Manager connects to the Smartcrypt Cloud to receive changes. Default is 60. Click the pencil to edit this interval. |
Internal (Agent) Polling Interval (seconds) | How often the Smartcrypt clients deployed in your organization will check with the SEM for changes. The changes could be new Smartkeys, new policy changes, or account access changes. |
| Administrator Idle Session Timeout (minutes) | Use this field to specify when (in minutes) the server should automatically logout an administrator's session. The default (999) is unlimited. |
| Enable Service API | Sometimes you may need to have the Smartcrypt Manager online, but not accessible to all the clients. The most common time you may need this is when migrating servers, or when performing upgrades on components. When you say No, only connections from the system will be accepted. External web requests will be rejected. Applies to all SEMs in a cluster. |
| Local Enable Service API | Sometimes you may need to have the Smartcrypt Manager online, but not accessible to all the clients. The most common time you may need this is when migrating servers, or when performing upgrades on components. When you say No, only connections from the system will be accepted. External web requests will be rejected. Applies only to the SEM this setting is changed on. |
| Local Database Paused | Use this for troubleshooting. When you click Yes, database access is temporarily suspended. All current users are logged out. Only locally defined administrator accounts are available. |
| API Throttle Percentage | When configured, the percentage of agents which will be allowed to log into Smartcrypt. Use when extreme load is preventing administrators from connecting to the SEM during troubleshooting. |
| Manager Allowed IP Addresses | Identify IPv4 addresses for a whitelist. |
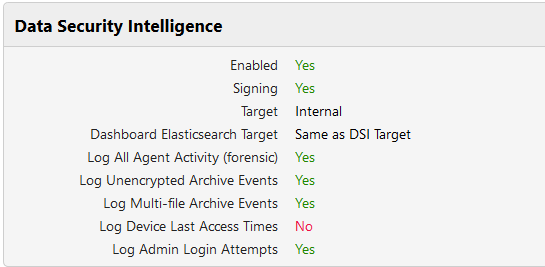
Data Security Intelligence
Data Security Intelligence enables Smartcrypt clients deployed in your organization to report back to the SEM a file audit log. It will transmit file encryptions, decryptions and different Smartkey access control list changes. See the Reporting (DSI) page for detailed documentation.
This feature will collect data about how your users are using the system. Each file encryption and decryption is logged, so leaving this option enabled without interest in this feature will cause your database to grow very large very fast.
| Setting | Description |
|---|---|
| Enabled | Server will perform Data Security Intelligence functions. |
| Signing | Clients will transmit information about digitally-signed files as well as encryptions. |
| Target | Identifies where DSI data will be sent. Identify an internal location, a Splunk server, or an appropriate system log. |
| Dashboard Elasticsearch Target | To include DSI events in the Dashboard view, click here and check Enable DSI in Dashboard. You can choose the target set in the previous line, or choose a different URL. |
| Log all Agent Activity (forensic) | Clients will transmit information everything each client does. |
| Log Unencrypted Archive Events | Clients will transmit information about all archives created and extracted, even when the archive is not encrypted. |
| Log Multi-file Archive Events | Clients will transmit information about all archives created and extracted containing more than one file. |
| Log Device Last Access Times | Clients will transmit when a device was last accessed. |
| Log Admin Login Attempts | Clients will transmit when an attempt to login to that device as an administrator. |
Configuring the Smartcrypt Enterprise Manager to connect to your mail server
As your users begin to use Smartcrypt and Smartkeys, notifications and alerts can be sent via emails. These emails will alert a user to a request for access to a Smartkey. The requester will receive an email when access is granted, and the owner of the Smartkey will receive an email alerting them to the pending request. To get the email notifications setup within your organization, just configure the mail settings.
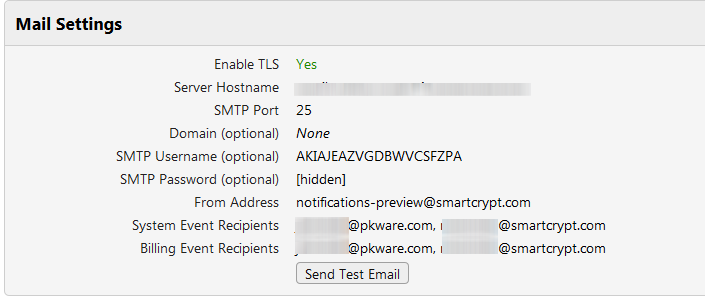
| Setting | Description |
|---|---|
Enable TLS | Require mails to be secure |
Server Hostname | Mail Server hostname |
Port | 25 by default, unless TLS enabled |
Domain | If your mail server requires authentication, identify the Active Directory Domain here. |
SMTP Username | (Optional) If your mail server requires authentication, enter the Active Directory user name. |
SMTP Password | (Optional) If your mail server requires authentication, enter the Active Directory user password. |
From Address | Enter what should appear in the From: line when Smartcrypt Enterprise Manager sends log reports |
System Event Recipients | Enter the email addresses for people who should be notified when high priority errors occur on SEM. |
Billing Event Recipients | SEM checks periodically for license consumption usage and will notify this person when the allocated license count is reached and when the system will stop distributing new licenses to Smartcrypt clients. |
When you have configured the Mail Settings, click Send Test Mail to confirm that everything works.
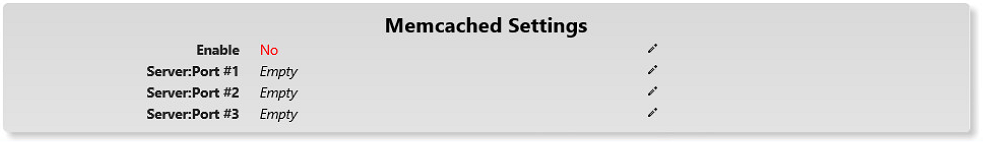
Configuring the Smartcrypt Enterprise Manager to use Memcached
As your environment may be very large, we recommend running different SEM application servers behind a load balancer. Using and configuring a load balancer will help the system scale to handle more HTTPS traffic from the clients in your organization. This type of configuration is for large-scale deployments where the SEM would be needed to serve 100,000 clients throughout an organization. Memcached is required when using more than one SEM in an application server cluster. When Memcached is configured, it will store data in itself, instead of in memory on the single SEM. Memcached can be configured to be accessed from multiple application servers to create a shared cache pool.
Enable | Defaults to No. Only required to enable if you need more than one Smartcrypt Enterprise Manager in your cluster |
|---|---|
Server:Port # | This is a combination of the server address and the port that Memcached is installed and running on. It is important to verify that your Smartcrypt Enterprise Manager has the correct ports opened on through any possible firewall. |
.png)