Lockers
Description
Lockers provide automatic, persistent folder protection across any file system in your environment. When creating a locker on a device, an administrator needs to define details for how the locker will be configured. If the file system can be mounted by a client that can run PK Protect, a locker automatically protects the data on the volume. Set up lockers on this page. As soon as the locker information syncs to the PK Protect client device, anything placed in the locker will be protected.
Existing lockers
When you browse to the Lockers tab, the default view will display all lockers defined on the devices in your Smartcypt ecosystem. The main view displays:
- Name and email address of the locker's user (Owner)
- The name of the device in the PK Protect universe
- The platform/operating system of the device hosting the locker
- Paths to the protected volume(s) on that device (see table in the next section)
- Whether the locker is a valid location and is able to be encrypted.Click the number in the Compliant or Not Compliant column to see details about the locker. See .Lockers v18.4#Compliance for more information.
- To temporarily make this Assignment Scan-Only (see following table), click Disable.
To display what Smartkey is being used, click Edit to view the details.
Locker Compliance
The Compliant and Not Compliant columns in the Lockers list indicate if the agent has received the latest policy changes from the PK Protect Enterperise Manager.
Viewing the Status of Existing Lockers
Click Status to view additional details about the selected Locker.
| Compliance | Offers a quick visual identification of problems. The green circle indicates the agent has received the latest PEM policy changes. The red circle indicates that the agent has not received the latest PEM policy changes. |
|---|---|
| Status | This field identifies any issues occurring in the agent. Possible issues include an invalid configuration or path/location. Click Edit to fix the problem. |
| Name | Name of the selected Locker(s) owned by the selected user. |
| Path | Location to be protected on the end points. |
| Size | Total size of protected file(s) and folder(s) on this device. |
| Files | A count of protected files. |
| Folders | A count of protected folders |
| Plaintext | A count of un-encrypted text files in the protected Path. |
| Encrypted | A count of encrypted files in the protected Path. |
| Sensitive | A count of sensitive files in the protected Path. |
| Reported At | Date and time of this status report. |
New Locker
Click Add to display this Device Search page: Enter relevant data in at least one field to locate the device you want to make a Locker on.

Complete the form to set up a new locker. This page also appears when you click Edit on an existing locker.
Common Attributes
| Field | Description |
|---|---|
| Name | Name of the selected Locker(s) owned by the selected user. |
| Path | The path is the exact folder path on the remote device to be set up as a locker. You may use a Universal Naming Convention (UNC) path. If the path doesn't exist on the specified device, the PK Protect client will try to create the path. If the path is invalid (for example, by referring to a path without permissions to access) no locker will be created. Do not place an Assignment in the same path as a Locker! This can lead to a variety of behaviors. |
| Smartkey | Select a Smartkey from the drop-down menu to encrypt the locker's files. Since we have defined a user and a device to set up the locker, the Smartkey list will be narrowed to Smartkeys the Locker user has access to. If the Smartkey you prefer to use does not appear in the menu, ensure that the locker user has access. |
| Whitelist | (Optional) By default, PK Protect will encrypt every file placed in the Locker. With the Whitelist, you can restrict the number and type of files encrypted in the folder. For example, if you only want to encrypt spreadsheets in this locker, type *.xls* in the whitelist. In the figure above, only files with a .dropbox extension in the user's Dropbox\Accounting folder is encrypted. All other files placed in this locker will remain unencrypted. When defining a set of whitelisted items, separate each file or extension with PEMicolons. If a whitelist is defined, ONLY the extensions matching the whitelist will be encrypted. |
| File Filter | Select from the drop down of available file filters created in the Discovery File Filters page. The file filter selected here will only be applicable to the base functionality of Encryption, Decryption, and Discovery. For more information on file filters, see the "File Filter" section in the discovery page and further below this page for discovery functionality of multiple remediations with file filters. |
| Compress | This option only appears when the "Mode" is set to "Encrypt" |
| Scan-Only Mode | Check this box to assess the size of a potential remediation project. PEM will scan the target system and provide you, the admin, with progress information (in % form) as the scan continues. |
| Report Compliance and Status | The locker will communicate its status to the PK Endpoint Manager, generating a report if the agent running the locker has not received the latest PEM policy changes |
| Report Advanced File Attributes | File Created Date, Created By, Last Saved Date, Last Saved by is reported to DSI when applicable. Note: This does not work for client agent older than 15.9 |
| Image Discovery | Checking this box will allow agents to discover sensitive information within supported image file types. |
| Exclude Hidden Files | By default, a locker will not encrypt hidden files. If you want to encrypt hidden files located in the locker, uncheck this option. |
| Exclude System Files | By default, a locker will not encrypt Windows system files. If you want to encrypt system files located in the locker, uncheck this option. You can verify system files by looking at the attributes of a file to confirm if it is deemed a system file. This protection only exists on Windows-based operating systems. |
| Report Successful Encryptions | If Data Security Intelligence is enabled on the Basics page, each file added or changed in the locker, will be reported in the Audit Log. That can generate thousands of events. Uncheck this option If your organization is not interested in the encryption events that will be generated by a locker. |
| Report Encryption Failures | A locker might fail to encrypt a file on the initial attempt. This might be caused by the file being locked open, or some other environmental issue. The PK Protect Locker service will attempt to encrypt the file again, but if your organization is interested in the failures being reported, enable this option. |
Discovery
Discovery Lockers use PK Protect Discovery to scan the contents of un-encrypted documents to determine remediation actions. To learn more about how to setup PK Protect Discovery, see Discovery.
| Smart Filter Bundles | The list of Discovery Filters to be used to scan data for matches on sensitive data. For more complex filtering, click . |
|---|---|
| MIP Labels | Discover on a specific MIP label by selecting a label from the dropdown list |
| File Filters | Select from the drop down of available file filters created in the Discovery File Filters page. The file filter selected here will only be applicable to the corresponding smart filter bundle and remediation in the same row. For more information on file filters, see the "File Filter" section in the discovery page |
| Remediation Actions | Remediation actions, defined in this table, are responsible for configuring the order of smart filter bundle(s) that are tied to specific remediation options. Remediation action order is important; the client agent processes the remediation actions list from the top down. The agent uses the first one that applies to its particular discovered action. Each row has a defined smart filter bundle that correlates to a remediation action defined in the discovery page. For example, a PK Protect assignment has two remediation actions. The first remediation action at the top looks for, “Secret” and has a remediation action to encrypt and move the file. The second remediation action below the first looks for, “Secret”+“Sensitive”, and remediates by deleting the files. If an assigned client finds “Secret” it will apply and only apply to the first remediation action at the top of the list by encrypting and moving the file. If an assigned client finds “Sensitive”, it will apply and only apply the second remediation action in the list by moving the file. If a PK Protect client older than 15.60.0046 is given an assignment with multiple remediation actions, the client will default to only using the top remediation action. |
Scheduling Options
Check the box to enable scheduling for an assignment. Select the "Start Time" and "Pause Time" based on the local machine's time for the period an assignment should be run in. Passive mode queues files to be processed even when outside of the schedule. Note: Agents earlier than 16.60 do not support scheduling.
Archive Options
Check the box to enable archive remediations for an assignment.
| Item | Description |
|---|---|
| Extensions | Archive file types that would be discovered and/or remediated on |
| Depth | The number of archive levels deep the assignment should execute in. If a file is within an archive that is within the top level archive, it would be placed at a depth of 2. |
| Preserve Signatures | Preserving the original signatures of an archive when the assignment discovers or remediates on the file |
Advanced Discovery Filters
Admins can use Boolean expressions to identify people and groups that expand beyond the limits of standard Active Directory Groups. You can select multiple Smart Filter Bundles, exclude some items with the NOT operator, and add others. In this example, the filter will search for all Personally Identifiable Information, but not credit cards or Social Security numbers.
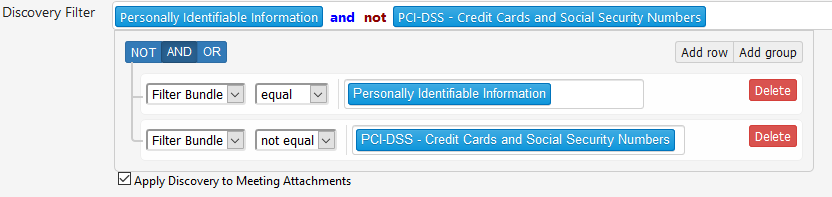
To generate this result:
- Click in the Smart Filter Bundles row to display your options. The icon changes to .
- Start typing the name of the bundle. PK Endpoint Manager will display a list you can select from.
- Click Add Row.
- To exclude a subset of information, change the second field to not equal.
- Again, type the bundle to select the information you want to exclude.
- At the top, change the Boolean operator. By default, the OR operator is selected. Change this to AND.
- Click outside the box to confirm the changes.
Re-encryption
Description
Re-encryption within a locker allows the PK Protect service the ability to change the encryption key protecting the archive file. The identity running the PK Protect Locker Service needs to have access to the existing key and the new key for re-encryption to work properly.
| Field | Description |
|---|---|
| Report Successful Re-Encryptions | When re-encryption is enabled, this reporting option will report a data security intelligence event when a re-encryption event occurs. An example of the event occurring would be in the use case of a file was encrypted with KEY A before entering the Locker folder, and is re-encrypted with KEY B by the Locker service. |
Report Re-Encryption Failures | When re-encryption is enabled, this reporting option will report a data security intelligence event when a failed re-encryption event occurs. An example of the event occurring would be in the use case of a file was encrypted with passphrase before entering the Locker folder, and is supposed to be re-encrypted with KEY B by the Locker service. If the re-encryption cannot occur a re-encryption failure event can be triggered. |
Performance Management
| Setting | Description |
|---|---|
| Periodic Scan Delay Max (ms) | Delay the first periodic scan for a random amount from 0 to the specified number |
| Queue Throttle | Controls the number items that are allowed to be in the pre-process queue |
| Queue Rate Amount | After this N number of items has been processed from the pre-process loop, sleep for X. (with X being defined in "Queue Rate Sleep") |
| Queue Rate Sleep | After N number (with N being defined in "Queue Rate Amount") of items has been processed from the pre-process loop, sleep for this X. |
Use Cases
Example Use Case
Setup - The PK Protect Locker Service is running as a Active Directory Service account "PKWARE". The PKWARE identity has access to Community Key A and Community Key B. The Locker is setup to enable re-encryption and to protect data with Community Key B.
| Scenario | Locker Action |
|---|---|
A file encrypted with Key A is added to locker. | The Locker will re-encrypt the file to Key B because the identity has access to Key A and Key B. |
| A file encrypted with Key C is added to locker. | The Locker will not re-encrypt the file to Key B because the identity does not has access to Key C. |
| A file encrypted with a passphrase is added to locker. | The Locker will not re-encrypt the file to Key B because the it requires a passphrase to decrypt. |
A file encrypted with a PGP Key or x509 certificate is added to locker. | The Locker will not re-encrypt the file to Key B because the it requires a certificate or PGP key to decrypt. |
Applying Multiple Keys to Lockers with Subfolders
PK Protect allows subfolders in a locker to be controlled by different encryption keys. The PK Protect Administrator just needs to create multiple entries for the Locker configuration for a device.
Example Use Case
Setup - There is a file server with files in the root directory ("P:\Shares\)" and subfolders than need to be controlled by different keys.
| Locker Path | Smartkey |
|---|---|
| P:\Shares | Key A |
| P:\Shares\Engineering | Key B |
| P:\Shares\HR | Key C |
To accomplish this, add three lockers with separate paths and Smartkeys:
- Click Add Locker.
- Identify the server and owner of that locker.
- Click Add Locker.
- Set the Path as P:\Shares.
- Set Smartkey to Key A.
- Set other parameters as required.
- Click Save.
- Repeat Steps 3-7 with the appropriate Paths for Key B and Key C.
- Click Done.
Now a file is placed into the following folders
| File Path | Action | Explanation |
|---|---|---|
| P:\Shares\test.txt | File is encrypted with Key A | The file is placed in the root folder of the "Shares" locker, which is controlled by the Locker Service, therefore it is encrypted with Key A. |
| P:\Shares\Engineering\test.txt | File is encrypted with Key B | The file is placed in the root of a subfolder which is controlled by the Locker Service, therefore it is encrypted with Key B. |
| P:\Shares\Engineering\Releases\test.txt | File is encrypted with Key B | The file is placed in the subfolder of the "Engineering" locker, which is controlled by the Locker Service, therefore it is encrypted with Key B. |
| P:\Shares\Accounting\test.txt | File is encrypted with Key A | The file is placed in a subfolder of the "Shares" locker, and not in the "Engineering" or "HR" folders, therefore it is encrypted with Key A. |
.png)