File Remediations
In PK Endpoint Manager (PEM), the Remediations > File tab is used to define remediation actions for files. These remediation actions represent the data protection options executed on a file(s) as part of the locker and assignment configuration. To access this tab, go to Remediations > File.
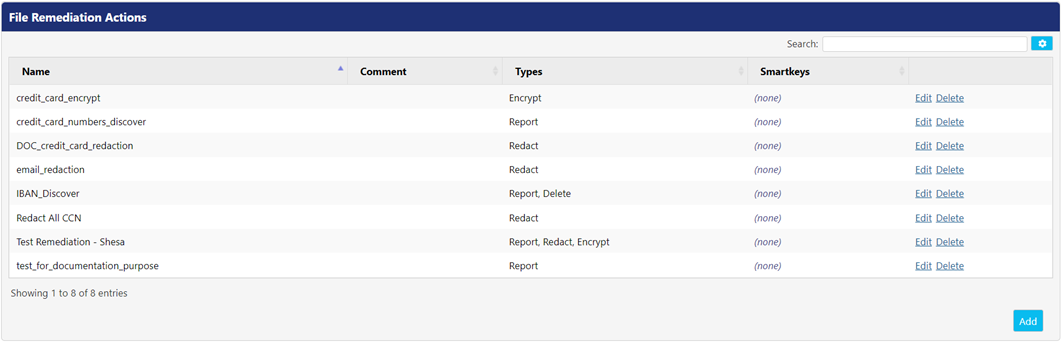
The File Remediation Actions panel allows you to add, edit, or delete the remediation actions. It displays the following UI controls on the screen for configuration.
- Click Delete button to delete a remediation action.
- Click Edit button to edit a remediation action.
Adding Remediation Actions
To add a new remediation, click the Add button to open File Remediation Action screen.
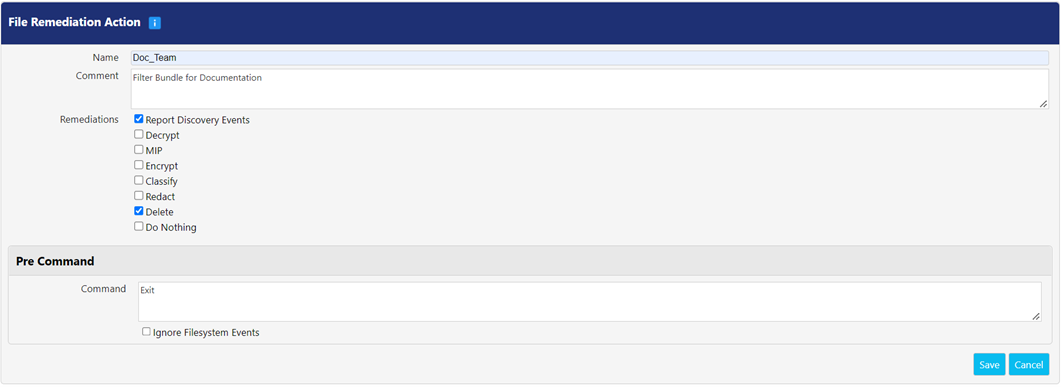
Perform the following steps for defining file remediation:
- Define a name for your file remediation action in the Name.
- Put comments, if any, in the Comment.
- Choose the desired Remediations by selecting the checkbox associated with the remediation name. For more information, refer the Remediation table.
- If applicable, enter a script to be executed in the Pre Command and Post Command For more information, refer Post Command and Pre Command.
- Click Save button to save the changes else, click Cancel.
Following is the description for each remediation action:
Description | |
Report Discovery Events | Check this checkbox to report an event when discovery action is triggered. |
Decrypt | Check this checkbox to select decryption as the desired remediation action. Following options appear when this option is chosen:
|
MIP | Check this checkbox to use Microsoft Information Protection (MIP) labeling as a remediation option. Following options appear on clicking this checkbox:
|
Encrypt | Select this checkbox to add encryption to your file remediation action. Following options appear when this option is selected:
|
Classify | Select this checkbox to include PKWARE classification in the file remediation action. When selected the following fields will appear:
|
Redact | Select this checkbox to include redaction in your file remediation action. Following options appear on clicking this checkbox:
Note: Certain file types, like Visio diagrams, cannot be redacted unless an appropriate editing software is installed on the same device as the redaction agent.
|
Delete | Select this checkbox to delete the file as part of your remediation. |
Do Nothing | Select this checkbox to perform no actions on the file. |
Pre Command
This panel allows you to input a pre-processing command in the Command field that can be executed on the targeted file(s). PK Protect will substitute any instance of `%FULLPATH%`, `%DIRECTORY%`, `%FILENAME%`, and '%BASEDIR%' in single-line commands with the respective details of the processed file. These four variables are passed as parameters in multi-line commands, in the order listed above. This panel consists of the following configurations.
- Classification SISL : Input the classification SISL script in this field to place a PKWARE classification label on a file before it is encrypted. The SISL can be found from Power Classifier for Files. Ignore Filesystem Events: On checking this checkbox, the discovery engine will ignore the changes made to the file by Pre-Encryption Command.
Post Command
This panel allows you to input a post-processing command in the Command field that can be executed on the targeted encrypted file(s). PK Protect will substitute any instance of `%FULLPATH%`, `%DIRECTORY%`, `%FILENAME%`, and '%BASEDIR%' in single-line commands with the respective details of the processed file. These four variables are passed as parameters in multi-line commands, in the order listed above.
- Classification SISL : Input the classification SISL script in this field to place a PKWARE Classification label on an encrypted zip file.
.png)