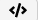MFA
Description
An attacker can access Smartcrypt data upon obtaining a user’s Active Directory account password and Smartcrypt email address. Requiring Multi-Factor Authentication (MFA) adds another obstacle to success for the attacker. Smartcrypt supports two methods of MFA: via a Smartcard/X.509 certificate, or through a Time-Based One Time Password (TOTP), where the user connects a device through a tool like Google Authenticator. Authenticator provides a code for the user to enter for a very limited time. This timing prevents an attacker from brute-forcing a code.
Client MFA Documentation
Creating a New MFA Policy
In Smartcrypt Enterprise Manager (SEM), go to Advanced > MFA to set MFA Policies. A list of existing MFA policies, including the Site-wide Default appears on this page. As with Policies set in the Archive section, the Site-wide Default covers users and groups not defined in another policy.
Click Add to create a new user MFA policy.
General Settings
- Type a Name for the Policy, and select the users and groups to apply this policy to. You can use 7362464 to identify users and groups.
- Check Require MFA to force MFA under specific circumstances.
- Check Notify user to add MFA to remind a user who has not set up a second device with TOTP yet. SEM cannot create a TOTP connection.
- The Mode setting defines where MFA is required.
- Server validates MFA on SEM, through certificates or TOTP.
- Client allows for local validation through proof of digital signature.
- Both Attempt to validate at SEM but allows client authentication if the client is offline.
- Grace Period (seconds) defines a period where a client activity can be completed and a user won’t be asked to perform MFA.
Setting | Modes | Description |
|---|---|---|
Account Transfer | Server* Off | User signs in to a new device (desktop or mobile), or after a password change on any device. |
Login | Server Client Both* Off | User logs in on a previously registered device. If the policy is set to Server, users cannot login offline. |
Encrypt/Decrypt | Client* Off | User receives a Smartcrypt file, or creates a new encrypted file. Note: This option is only applicable to certificate settings and not TOTP settings. |
Modify MFA Setting | Off Server* | This setting protects existing paired devices from attack by requiring an MFA connection before managing devices. Turning this option off would allow someone with the user’s credentials to remove any existing devices without having to prove access to that device. Policy for Certificates Only: User is required to provide certificate (Smartcard). The SEM will not allow user to continue on an MFA action without it. Policy for TOTP Only: User is allowed to do all actions, even if they are MFA based events. Until 1 pair exists, no MFA pair is required. Policy for Both TOTP and Certificates: User is required to provide certificate (Smartcard). The SEM will not allow user to continue on an MFA action without it. |
Advanced Definitions of Users and Groups
Admins can use Boolean expressions to identify people and groups that expand beyond the limits of standard Active Directory Groups. You can select multiple users and groups, exclude some users with the NOT operator, and add other users
In this example, the LargeData Marketing group is the Group that this policy applies to, but the group excludes user mig1@qanet.com.
To generate this result:
- Click in the Users/Groups field to display your options. The icon changes to .
- Start typing the name of the User or Group to apply this policy to. Smartcrypt Enterprise Manager will display a list you can select from.
- Click Add Row.
- In the left-most field, change to User.
- To exclude a user, change the second field to not equal.
- Start typing the user name and select the user you want to exclude from this policy.
- At the top, change the Boolean operator. By default, the OR operator is selected. Change this to AND.
- Click outside the box to confirm the changes.
Certificate Settings
If you use certificate-based authentication (through Smartcard or other means), check Allow Certificate-based Authenticator to enable that operation. These settings control how to implement and control interactions with digital certificates.
| Setting | Description |
|---|---|
Subject Filter | The Smartcrypt agent will search for keys using the Subject value |
Issuer Filter | The Smartcrypt agent will search for keys using the Issuer value. Example: |
Ignore Time Limits | Check this box to have SEM skip checking for expiration date and time nesting on certificates |
Match Certificate to User | By default, SEM will query Active Directory for these items. Clear the box to ignore queries on UPN, Email or Serial Number. |
Match UPN | SEM queries AD for the User Principal Name and only accepts a certificate if the UPN in the certificate matches AD |
Match Email | SEM queries AD for the user’s email address and only accepts a certificate if the email address in the certificate matches AD |
Match Serial Number | SEM queries AD for the user’s serial number or GID and only accepts a certificate if the Serial/GID in the certificate matches AD |
Custom Messages | Admins can customize the message box text to users when certain circumstances exist. Leaving a Custom Messages field blank will deliver the default message for the situation. |
No Certificate Pairs are installed | This message displays when no certificate-based authenticator is connected to SEM. |
TOTP Settings
Check Allow TOTP Authenticators to allow users to use a Time-Based One Time Password (TOTP) as a valid token. Admins can then customize the message box text to users when certain circumstances exist. Leaving any of the Custom Messages fields blank will deliver the default message for the situation.
- Prompt for TOTP: Enter a TOTP code
- No Pairs – Can Create: Not currently used
- No Pairs – Cannot Create: The Smartcrypt mobile apps (iOS and Android) display this message if a user logs in, but uses only a certificate to authenticate.
Check Certificate
Click Check Certificate to confirm whether a user certificate registered with SEM complies with the default site-wide policy.
You can either type an existing Smartcrypt user name in Fill User Info or upload the certificate file you wish to test to Choose Cert File.
You can also optionally confirm whether the certificate file will work to authenticate a device with Smartcrypt. Check the Check if acceptable to create MFA Pair box.
Click Submit to test the Universal Principal Name, email address, serial number, and assigned policy.
Manage PKCS11 Drivers
Smartcrypt users must set up a PKCS11 configuration before using Smartcrypt with MFA. Because the locations of PKCS11 libraries can vary, SEM provides the ability to define commonly used locations. The Smartcrypt Agent will fetch the list from the SEM and look for the proper PKCS11 libraries when making a MFA pair. Click, Manage PKCS11 Drivers to navigate to the PKCS11 Drivers page.
Manage Multi-factor Authenticators (SEM)
Administrators can disable or delete existing devices from the MFA page where a device is lost or stolen.
Use the Lookup feature to locate a system user. SEM displays a list of all MFA-authenticated devices for this user.
| Setting | Description |
|---|---|
| Name | Name of the authenticator |
| Enabled | Whether the device is active in the system. Click the link to Disable the device. |
| Kind | If the authenticator is a certificate or TOTP |
| Updated At | Date of last authentication |
Click Delete to permanently remove the device from Smartcrypt.
.png)